How your phone’s apps and features can be used to spy on you
Smartphones have many built-in sensors, and you may be surprised at what app developers do to gain access to them and your personal details, as Talking Point discovers.
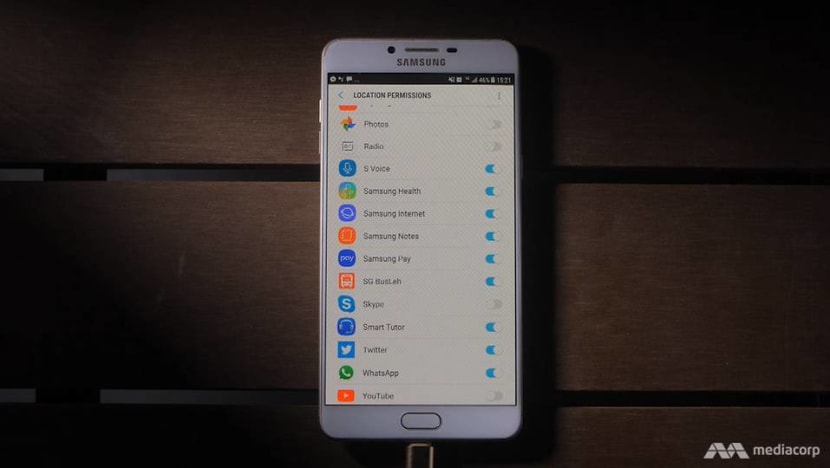
Consumers who do not take app permissions seriously may be allowing developers access to information in their phone.
SINGAPORE: Technology writer Lai Zit Seng has used voice-activated apps for three years now, but avoids using voice commands when confidential information is involved. He does not want his mobile devices spying on him and violating his privacy.
He is not being paranoid. In the middle of an interview with Talking Point, his Google Home device activated itself and said, “Okay, now by Paramore, here it is on Google Play Music.”
Talking Point host Diana Ser may have been surprised, but not Mr Lai.
“It happens often enough, even when I’m speaking to my colleagues in the office, and occasionally this thing will wake up,” he said, pointing to the device, which uses a voice-activated technology similar to Google Assistant on smartphones.
Such voice-activated apps are like hot mics waiting for instructions, which means they listen in on their users’ conversations. But Mr Lai is concerned that they do more than that. He questioned:
If a smartphone can be always listening for trigger words, then why can’t it also record and send audio all the time?
It can, and Talking Point discovers how it is done and what users should beware about to prevent their phone spying on them. (Watch the episode here.)
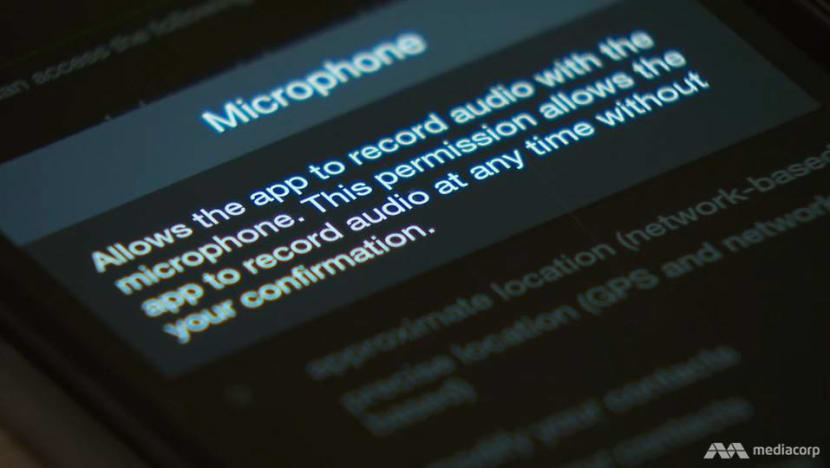
SECRET MIC ACCESS
Smartphone voice recognition arrived in Singapore in 2011 through Apple's Siri, which consumers can use to search for answers, set reminders and fix appointments, among other things.
This technology has since grown in sophistication. And in the past few years, voice-activated personal assistants like Amazon Echo and Google Home have become the rage.
While tech companies like Apple and Google have denied recording consumers without their knowledge, they admitted to keeping copies of consumers’ questions and commands to improve their services for those who use their personal assistants.
However, Siri and Google Assistant are not what should worry consumers, said Mr Desmond Heng, the project director at app developer Orfeostory. The real offenders, he warned, are apps that secretly activate one’s mic to record even an intimate conversation.
An app developer can create a calendar app, for example, which could start recording once the user inputs a calendar reminder. To illustrate his point, Mr Heng’s team created a news app that secretly embeds access to a phone’s mic.

When the user opens the app and reads an article, the app can start to record conversations, which are stored on the developer’s back-end server and can be downloaded and played back.
APPS THAT INVADE PRIVACY
A phone’s mic, however, is not the only gateway to one’s life. The average smartphone contains up to 14 sensors, each packed with information about the user.
A gyroscope keeps track of the phone’s position and orientation in the user’s hands and pockets. A light sensor monitors how bright it is where the user is, and an accelerometer tracks how fast one is travelling.
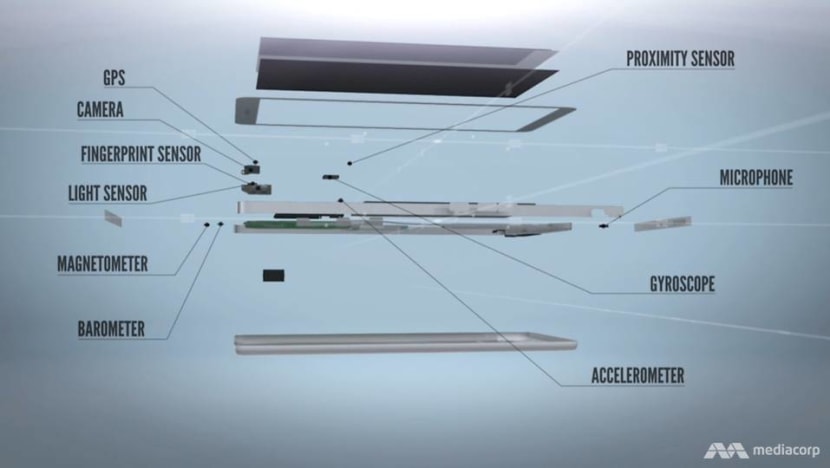
Some sensors can reveal sensitive personal details. The Global Positioning System, for instance, is very useful for locating users and providing them with directions to another location. But app developers could exploit this feature.
In 2013, it was discovered that a flashlight app was secretly amassing its users’ locational data, which was sold to advertisers in a massive privacy breach.
Mr Paul Mah, who has been writing about tech gadgets for 20 years, said there are many unrelated apps that might ask for one’s location, like flashlight apps and even Tetris games.
A 2015 survey found that 58 per cent of local Android apps in the Google Play store requested excessive permissions – for information unrelated to their functions – and 70 per cent wanted access to the phone’s location feature.
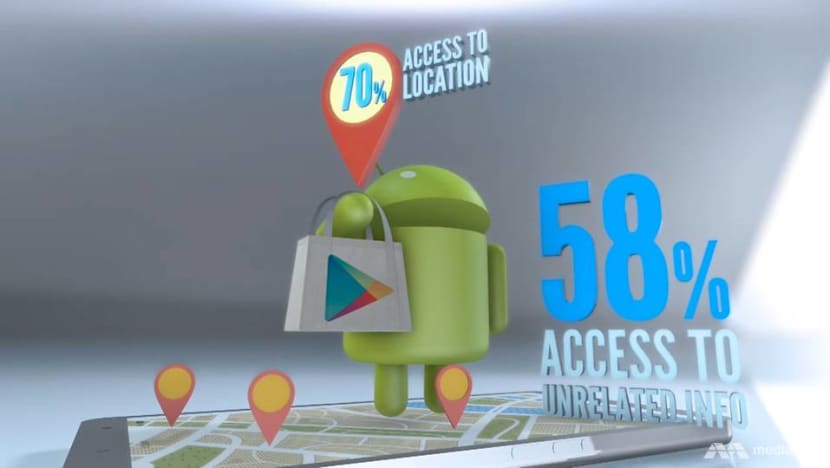
Said Mr Mah: “In certain cases, (the developers) can use it to build a profile of the user. In other cases, they might actually be reselling the data to third-party providers.”
By using the location history on a friend’s phone, Mr Mah himself was able to pinpoint the places the person went to the whole week, such as his office, and even his mode of transport.
“While he does travel by vehicle, most of the stops are not at car parks. So probably it’s Uber, Grab or a taxi,” deduced Mr Mah.
(Read: Your phone number is all a hacker needs to track you, steal your info)
THEY CAN FIGURE OUT YOUR PIN
There are rules governing the collection of personal data, but consumers are often guilty of allowing developers to access these sensors by not taking app permissions seriously.
One way to prevent apps from harvesting this information is to restrict their access to one’s mic and GPS via the phone settings.
But that will not completely secure one’s personal data. Most of these sensors lack permission controls, which means anybody could potentially access the information.
Senior research scientist Shivam Bhasin, from Nanyang Technological University’s Temasek Laboratories, showed how a developer or even a hacker could figure out someone’s personal identification number by monitoring the phone’s sensors.

For example, if a user is going to press the number two, the phone could be positioned relatively flat. But if the user reaches for the number five next, he would be moving the phone in a certain direction.
Similarly, the phone would tilt as the user goes from the number five to the number four or six.
“All these movements are captured by the sensors. And once we’re able to capture this information, we feed it to some machine-learning algorithms, and then they’re able to give us the PIN,” said Dr Bhasin.
It’s not only the hackers, but all the apps that are installed on your phone would have access to this information.
The NTU researchers achieved a 99.5 per cent success rate in recovering the 50 most common PINs (for example, 1234, 2580 and 4321).
WATCH: Unexpected ways your privacy might be comprised (Dur 2:59)
DIGITAL DILEMMA OR NO?
As smartphones evolve from communication devices into surveillance tools, some ordinary people are using phones for that very purpose.
Entrepreneur Syed D Jailani, a father of three, has installed a monitoring app on his children’s phones, giving him access to their locations and allowing him to track their daily routes, even routes from weeks past.
He is not bothered if an app developer can track his movements on his phone in the same way. “I don’t see this as a huge intrusion into my privacy,” he said. “I’ve got nothing to hide to start with.”

But how about developers using the data on his phone to crack the PIN for his bank account?
“I choose not to live by those fears,” he said. “I believe the proper authorities would have their security measures in place for that kind of thing. So that would leave me with some peace of mind.”
For others, however, the digital dilemma may only get worse as they become more reliant on smartphones.
“Privacy is definitely one of the big concerns,” said Mr Lai. “It may even feel very creepy, right – that (our conversations) are being recorded?”
Watch this episode of Talking Point here. New episodes every Thursday at 9.30pm on Mediacorp Channel 5.