Android users lose about S$100,000 CPF savings to malware scams in June
.png?itok=Gl5MsFpK)
An advertisement for seafood on Facebook which was a victim’s first contact point
with the scammer. (Photo: Singapore Police Force)
SINGAPORE: Users of Android devices have lost at least S$99,800 (US$74,400) of Central Provident Fund (CPF) savings in June this year to malware-related scams.
In a news release on Saturday (Jun 17), police noted that at least two reports of such cases have been received this month.
"The police would like to alert members of the public using Android devices on the emergence of scams involving malware which resulted in losses from victims’ CPF accounts as well as bank accounts," police said.
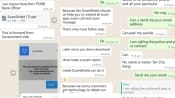
According to the police, victims would come across advertisements for groceries via social media messaging platforms such as Facebook.
After contacting the scammers on Facebook or WhatsApp, the victims would receive a uniform resource locator (URL) to download an Android Package Kit (APK) file to order groceries and make payment.
APK is an application created for Android’s operating system.
"Unknown to the victims, the application would contain malware that allowed scammers to access the victims’ device remotely and steal passwords, including passwords (for example, Singpass passcode) stored in the device," said police. "The scammer might also call the victim to ask for their Singpass passcode, purportedly to create an account on the application."
Victims would then be directed to fake bank application websites to enter their banking credentials to make payment. The malware, with keylogging capabilities, would capture the victims' credentials.
Scammers would then be able to remotely access the victims' CPF accounts using the stolen Singpass passcode and request to withdraw the CPF funds via PayNow.
"Once the CPF funds are deposited into the victims’ bank accounts, the scammer will access the victims’ banking application and transfer the CPF funds away via PayNow," said police.
Victims would only realise they had been scammed after discovering unauthorised transactions in their bank accounts.
"The police would like to remind members of the public of the dangers of downloading applications from third-party or dubious sites that can lead to malware being installed on victims’ mobile phones, computers, and other Information Communications Technology devices," said police.
"Scammers will trick victims into installing malware-infected applications that are outside the app store. Members of the public are advised not to download any suspicious APK files on their devices as they may contain phishing malware."
Precautionary measures
- Add: Anti-virus or anti-malware applications to your device. Update your devices’ operating systems and applications regularly to be protected by the latest security patches. Disable “Install Unknown App” or “Unknown Sources” in your phone settings. Do not grant permission to persistent pop-ups that request for access to your device’s hardware or data
- Check: The developer information on the application listing as well as the number of downloads and user reviews to ensure it is a reputable and legitimate application. Only download and install applications from official app stores such as Google Play Store for Android
- Tell: Authorities, family, and friends about scams. Report any fraudulent transactions to your bank immediately
For more information, the public can visit www.scamalert.sg or call the Anti-Scam Hotline at 1800-722-6688.
Those with information relating to scams can call the police hotline at 1800-255-0000 or submit online.
The public can also visit CSA's singCERT advisory to find out more about malware and the steps they can take to protect their mobile devices.