Man gets jail for filming malware tutorials for syndicate; 129 Singapore victims lost S$3.2m
The malware enabled scammers to take over the phone or access applications in order to make outgoing bank transfers.
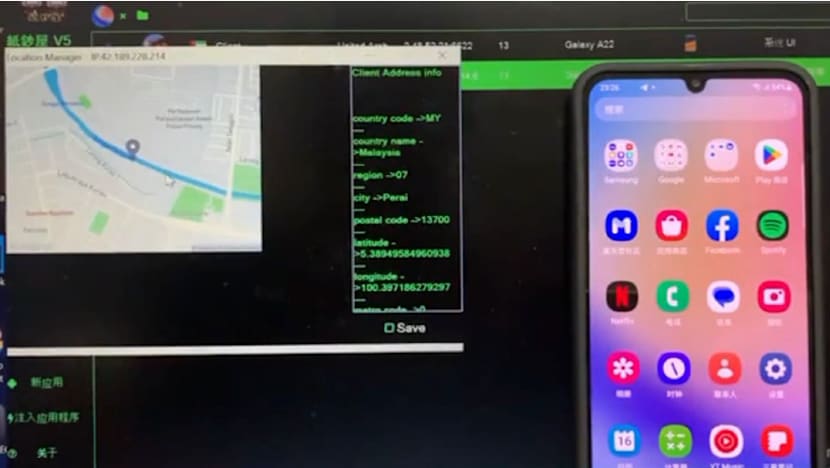
Screen capture of a tutorial video demonstrating the use of Spymax malware to access the location of a mobile phone via GPS. (Photo: Court documents)

This audio is generated by an AI tool.
SINGAPORE: A Malaysian man who was roped into a criminal syndicate by a Taiwanese man he met in a Korean prison recorded videos teaching syndicate associates how to use malware that could allow remote control of Android mobile phones.
As a result of the syndicate's efforts, 129 victims in Singapore lost about S$3.2 million (US$2.5 million), after their phones were remotely accessed and unauthorised bank transfers were made via their mobile banking applications.
Cheoh Hai Beng, 49, was sentenced to jail for five-and-a-half years and fined S$3,608 on Tuesday (Dec 9).
He pleaded guilty to two charges of being a member of a criminal syndicate and conspiring with others to use software hosted in servers to control Android mobile phones in Singapore.
A third charge was taken into consideration for sentencing.
The case is believed to be the first prosecution here of a person for teaching others how to use malware.
THE CASE
Cheoh met Lee Rong Teng, a man from Taiwan, while they were both serving jail terms in South Korea in 2008.
They became friends and Lee, who is still at large, invited Cheoh and his wife to visit him in the Dominican Republic sometime before Mar 20, 2022.
Cheoh was unemployed at the time and joined Lee in the Dominican Republic, but his wife was unable to join them as she was in China and the country was in lockdown because of the COVID-19 pandemic.
Lee asked Cheoh to continue keeping him company until his wife could join them, agreeing to pay for Cheoh's living expenses and fines he would incur when his travel visa expired.
Cheoh wound up living in the Caribbean nation for just over a year.
In January 2023, Lee told Cheoh that he had been introduced to a software which allowed users to "spy on people's phones".
He showed Cheoh several versions of the software and asked him to learn how they functioned.
The software was a type of highly sophisticated remote access Trojan tool, colloquially known as "Spymax" malware, designed to be installed in Android mobile phones, the court heard.
Once installed, the malware can be controlled remotely, with a third party gaining unauthorised access or modifying the mobile phone contents without authorisation.
In order to remain undetected by the phone owners, the software was designed to masquerade as legitimate Android applications for innocuous purposes such as online shopping, said the prosecution.
After Cheoh had taught himself how to use the software, Lee asked him to record videos teaching viewers how to use the malware.
He said this was for him to attract potential "business partners" and "customers" he could sell the malware and tutorials to.
Cheoh knew what the malware could do. He had heard Lee speaking to a Malaysian "business partner" about using the malware to conduct scams on Android mobile phones in Singapore.
While initially reluctant to record the tutorial videos, Cheoh agreed after Lee promised to pay him and after he threatened to release a video he had recorded of Cheoh demonstrating the use of the malware.
Lee also said Cheoh need only help him until Lee could find someone else to record the videos.
RECORDING THE TUTORIAL VIDEOS
From February 2023 to April 2023, Cheoh used phones provided by Lee to record tutorial videos demonstrating the Spymax malware.
The videos showed how to set up the malware and to perform functions such as remotely accessing cryptocurrency applications, capture passwords of crypto wallets, remotely access camera applications, access contact lists and SMS history, and ascertain the location of the phone via GPS.
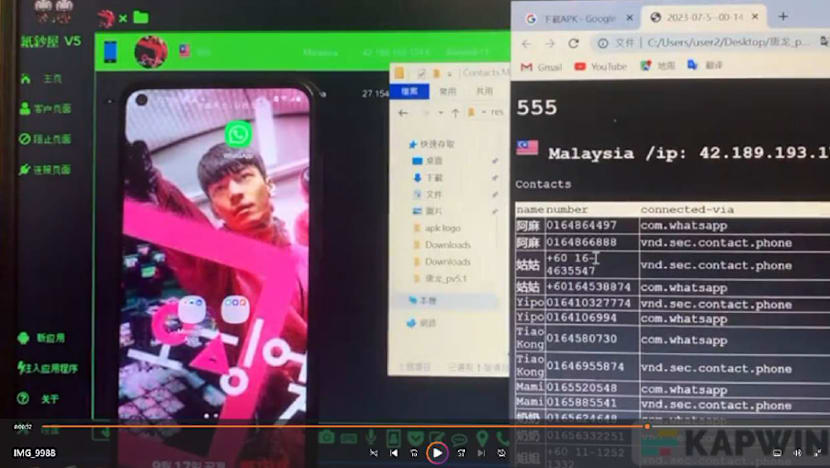
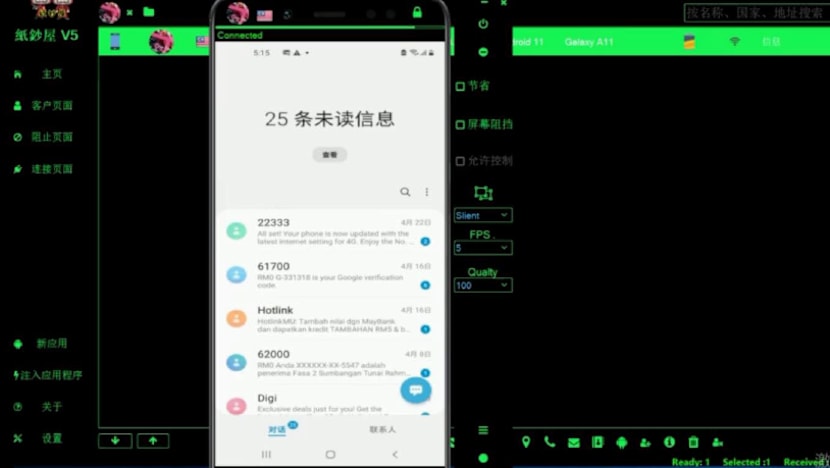
Cheoh sent the videos to Lee, who disseminated them to his "business partners" and customers.
Cheoh returned to Malaysia on Apr 11, 2023 when Lee agreed to let him leave even though he had not found a replacement. He brought with him two laptops and two phones and later recorded more tutorial videos at Lee's request while in Malaysia.
After this, Lee arranged for the devices to be collected from Cheoh outside a supermarket in Penang.
In total, Cheoh recorded at least 20 tutorial videos operating the malware between February 2023 and May 2023. He received US$700 in February 2023 and US$1,000 from Lee for his work during March 2023 and April 2023 respectively.
Other members of the syndicate later used the malware to conduct scams on people in Singapore.
Discussions were held to create landing pages online from which unsuspecting victims could be lured into downloading applications containing the malware.
There was also an office in Malaysia where the operation of the malware was supervised.
Between June 2023 and June 2024, Android mobile phones belonging to at least 129 victims in Singapore were remotely accessed after their phones were installed with versions of the malware.
Their phones were taken over and unauthorised outgoing transactions amounting to at least S$3,197,974.24 were made from their bank accounts via the mobile banking applications in their phones.
Cheoh was arrested at his home in Penang on Jun 12, 2024 by the Royal Malaysian Police, in collaboration with Singapore's Technology Crime Investigation Bureau of the Criminal Investigation Department, for his suspected involvement in malware-enabled scams against Singaporeans.
He was later escorted to Singapore and held in custody.
SENTENCING ARGUMENTS
Deputy Public Prosecutor Hon Yi sought 72 to 85 months' jail for Cheoh, along with a fine of S$3,608 to disgorge the profit he made from the offences.
He said there had been no previous prosecutions for a person who teaches others how to use malware, but cited other cases that involve sophisticated criminal enterprises or syndicates.
"There is a saying - give a man a fish, and he eats for a day. Teach a man to fish and he eats for life," said Mr Hon.
"In this case, what the accused is doing is to teach wrongdoers out there how to use the malware for commission of other offences."
He said Android phones are used by roughly half the population, and said the potential harm was "a lot greater" and goes beyond even Singapore's borders.
"The organised criminal group in this case was clearly in the industry of carrying out scams, and the whole aim of it was precisely as what the accused did, to propagate their malware and let people use the malware on as many victims as possible," said Mr Hon.
He said the criminal group was transnational in nature and its scale was "not small".
Defence lawyer Sujesh Anandan argued that this was a "high harm, low culpability offence".
He referred to the prosecution's saying about teaching a man to fish.
"There's no evidence how many people exactly Mr Cheoh taught to fish," said Mr Sujesh. "What we do have is the total quantum involved."
However, he said there was no evidence how much of this quantum is related to the videos made by Cheoh.
He also highlighted how the group was actively scamming the victims from June 2023, after Cheoh stopped his involvement with the group in May 2023.
Mr Sujesh said Cheoh's involvement was limited to the filming of the tutorial videos, and he was on "the lowest tier of the hierarchy of the group".
He said Cheoh would not be able to pay the fine, and is legally aided through Pro Bono SG with the Criminal Legal Aid Scheme.
For conspiring to obtain unauthorised computer access to commit an offence, Cheoh could have been jailed for up to 10 years, fined up to S$50,000, or both.
For being a member of a locally linked organised criminal group, he could have been jailed for up to five years, fined up to S$100,000, or both.