Your phone number is all a hacker needs to track you, steal your info
They can also pose as free WiFi in public areas to hijack personal data. Talking Point explores how people need to protect themselves better from cyber attacks.
Text messages can be intercepted and phone cameras hijacked remotely by hackers.
SINGAPORE: The host of Talking Point Steven Chia was engrossed in conversation with a friend at a food court, oblivious to the fact that someone else was watching and listening in - via his own mobile phone on the table.
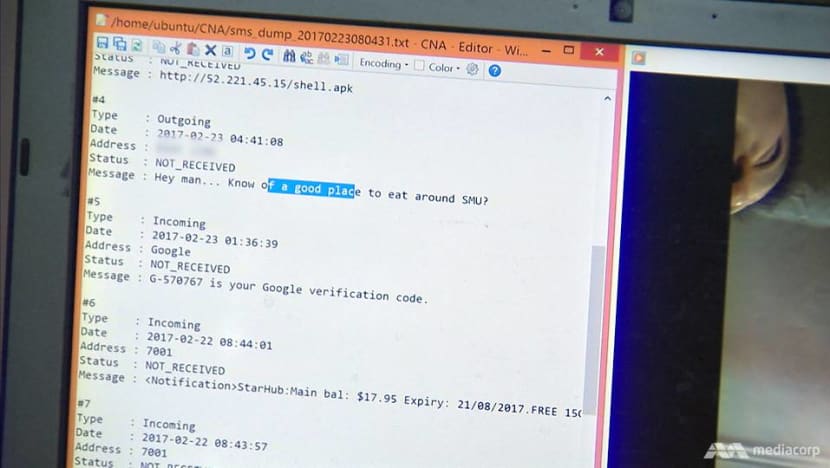
The hacker, who was able to manipulate the phone’s camera and other functions remotely, was able to pinpoint where Mr Chia’s lunch location was, and even read the contents of an SMS message that he had just typed out.
“Whatever you were doing, we had knowledge about it,” Mr Wong Wai Tuck told Mr Chia later. “While you were having lunch at Food Republic, we took a few pictures and a video. We also found out what you were talking about.”
Fortunately for the Mediacorp host, the ones who broke into his mobile phone were ethical hackers from the Whitehat Society at the Singapore Management University. The exercise was part of an experiment to show how hackers could easily compromise a mobile phone, starting with just the knowledge of its owner’s number.
WATCH: More on how your phone can be hacked (2:08)
In an era of hyper-connectivity, one in three Singaporeans does not have anti-virus software on their handphones, according to a survey by the Cyber Security Agency of Singapore (CSA). Some reasons cited were that they did not know the software exists, or that they simply did not see the need for mobile security.
This issue of how Singaporeans are not doing enough to protect themselves from cyber threats like ransomware and phishing attacks was discussed on a recent episode of Talking Point, a current affairs show on Mediacorp Channel 5.
BEWARE PUBLIC WIFI DANGER
For example, connecting to a free WiFi network in public places can be risky, as you may be open to a man-in-the-middle attack.
This is where a hacker uses his phone’s own hotspot to pose as a free WiFi network, and when you connect to it, it gives him access to your phone, personal files and credit card details.
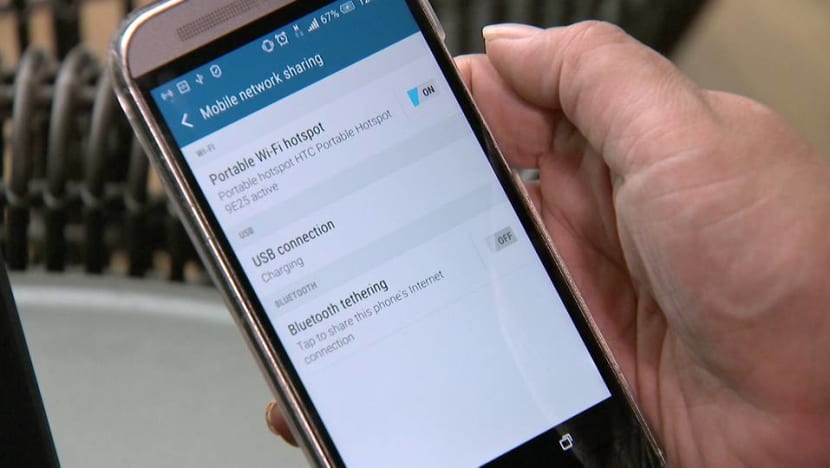
The CSA survey found that more than six in 10 respondents connect to such WiFi networks in public places, whether or not they are familiar with them. And, worryingly, a third of them make online purchases and conduct financial transactions on these networks.
This means that hackers could potentially access your sensitive information and sell them on the Dark Web, a hard-to-access part of the Internet often used for illegal activities.
Tom, a Dark Web operator who declined to give his real name for security reasons, said that a hacker can buy your stolen data and slowly build a profile around you, gathering your personal information, where you work and the credit cards that you own.
“After that, I can initiate a lot of attacks. For example, I can call your bank and say that I lost my credit card. I can impersonate you and do bank transactions on your behalf,” he said.

Mr Richard Koh, an industry partner of Cyber Security Awareness Alliance and chief technology officer of Microsoft Singapore, warned that “there is a huge urgency for us as a nation to learn more about what the threats look like and how to protect ourselves”.
Some measures include using strong passwords - a combination of characters, numbers and symbols - and religiously updating the operating system of devices.
Watch this episode of Talking Point here on Toggle.