'Incredibly easy to spoof': How SMS scams work and what can be done
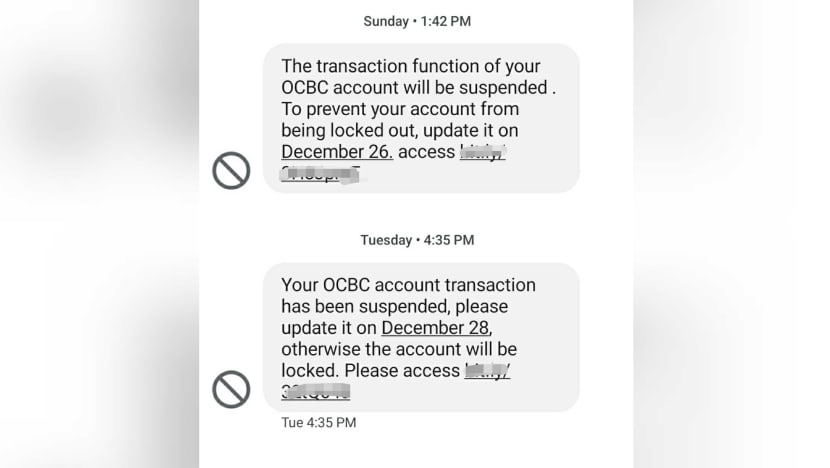
Screengrab of phishing scam messages impersonating OCBC, Dec 2021.
SINGAPORE: Once a popular way of communication, SMS, or short message service, has now surfaced as a weak link exploited by scammers.
With its vulnerabilities such as allowing malicious actors to replace any phone number with a spoofed name, SMS “has little to no security capabilities to manage the extent of the social engineering threats that we see today”, said Mr Clement Lee, a security architect at Check Point Software Technologies.
To plug the security gap, experts that CNA spoke to suggested that banks stop using SMS as a channel for authentication purposes.
But telecommunications firms and government agencies also have a part to play, they added, calling for stronger cooperation among all players.
"INCREDIBLY EASY" TO SPOOF AN SMS
In the recent phishing scam involving OCBC, victims received an SMS from scammers posing as the bank and claiming there were issues with their accounts or credit cards.
The message, which contained a link to a fraudulent website mimicking OCBC’s, appeared in the same SMS thread as genuine ones previously sent by the bank. This fooled many customers.
Nearly 470 people have lost at least S$8.5 million since last December.
This happened because malicious actors were able to make use of a hidden field within SMS – called the Sender ID – to mask their actual phone numbers and use an alphanumeric identifier instead, said Mr Ian Hall, head of client services for Asia-Pacific at Synopsys Software Integrity Group.
By taking on the name of a bank or any legitimate company, a fake SMS would then be grouped together with those using the same name in the mobile phones of recipients.
“This is actually incredibly easy to spoof since it is just an additional field in an SMS and can be added by attackers using simple API (application programming interface) calls to any SMS service providers,” Mr Hall said.
There are many SMS spoofing tools currently available online for free, said Mr James Lee, a security solution architect for Asia Pacific, China and Japan at US network security provider F5.
These tools are also widely used by legitimate companies for their SMS marketing campaigns, so that customers receive messages from a familiar name instead of an unknown number. The problem lies in the lack of verification by telcos that operate the current SMS system, experts said.
“Today, the sender information embedded into an SMS is not verified by telcos before being relayed to the recipient … Without any authentication process in place to ensure that SMS spoofs are done only by legitimate senders, phishing attacks via SMS have become easy to launch,” said Mr Lee.
The ease at which a fake SMS can be sent has also been documented by Mr ZP Lee, who goes by "Captain Sinkie" on his blog.
Mr Lee, founder of coding school Upcode Academy, said he became concerned after reading about recent phishing scams and decided to find out for himself how an SMS could be spoofed.
By using a third-party tool he found online, he managed to send a message to himself under the name of “DBS Bank”.
These third-party services are easily found online with the code written up “in mere minutes”, said Mr Lee, who is also a data science instructor.
“I’m astounded and extremely worried by how easy it is for anyone to use them to spoof the sender’s name in an SMS,” he told CNA.
MANDATE REGISTRATION OF SMS SENDER IDS?
Experts said making users pre-register their SMS Sender IDs, or the names that appear on their messages, with authorities is one way to thwart illegal attempts by swindlers.
In Singapore, a pilot programme allowing organisations to do so was launched by the Infocomm Media Development Authority (IMDA) in August last year. After registering, messages will be blocked when there is unauthorised use of the registered Sender IDs.
The programme, however, is not mandatory.
Mr Lee the entrepreneur has started an online petition calling for authorities to enforce such pre-registration and adopt "a whitelist approach".
“Restrict and block all sender names from being changed by a third party. Instead, require companies to register for certain sender names before they can be used to send SMS. This means that hackers will effectively be unable to spoof the sender names of SMS,” he explained.
As of Thursday (Jan 20) afternoon, nearly 2,200 people had signed the petition on Change.org.
Such pre-registration is already required in many countries, experts said.
“Pre-registration would prevent attackers from being able to spoof organisations' SMS Sender IDs. I would definitely be supportive of this being made mandatory by the Government,” Mr Hall said, adding that he does not see other regulations “that could help without being overbearing”.
The Government can also develop a platform that complements the existing ScamShield app, allowing organisations like banks to share phone numbers and malicious URLs that they have detected.
“This open database of information can help the companies stay ahead and defend against fraudsters who may reuse the same number or links in future attacks,” said Mr Lee, the cybersecurity expert from F5.
Beyond legislation, organisations like telcos and banks also have to play an active role in protecting consumers.
“While SMS spoofing tools play a role in enabling these impersonation scams, the current SMS system deployed by telcos also contribute to how fraudsters can easily exploit customers’ trust,” said F5’s Mr Lee.
When contacted by CNA, Singtel said since the rise of number-masking technology five years ago, it has been blocking incoming international SMS traffic with alphanumeric Sender IDs that are not officially routed through Tier 1 SMS aggregators.
Tier 1 SMS aggregators are the only aggregators licensed to facilitate commercial SMS traffic.
The telco estimates that it blocks about 40 million messages originating from overseas mobile operators each year.
A Singtel spokesperson told CNA the company supports IMDA’s pilot programme and believes that enforcing pre-registration for Sender IDs is an important measure against scam messages.
Similarly, StarHub said it has put in place safeguards to block potentially malicious messages sent from commonly spoofed numbers.
Over at M1, safeguards in place include working with authorities to take down scam sites and associated mobile lines where possible.
“We have also been working closely with IMDA on sector-wide measures such as blocking of commonly spoofed numbers, prefixing all incoming international calls with +65 to alert the public to potential scam calls and educating users to recognise and avoid scams,” a spokesperson said.
The telco also said that IMDA's SMS Sender ID protection registry provides "an additional layer of protection" and urged organisations to participate in the pilot programme "to assess its effectiveness".
BANKS URGED TO SCRAP USE OF SMS
Experts like Mr Lee from Check Point Software Technologies also suggested that banks scrap the use of SMS for two-factor authentication (2FA) or send alerts where the primary actions could be activated from a URL.
“Perhaps digital tokens should be mandated while SMS is only for back-up with additional authentication,” he said.
Mr Hall from Synopsys agreed that SMS should be phased out as a tool for 2FA, noting that other methods – such as in-app notifications and hardware tokens that are either standalone or built-in on mobile apps – have proven more secure.
Both experts also said SMS can remain as a notification tool, but banks would need to keep reminding customers to be vigilant and not to click on links embedded in these text messages.
Mr Yeo Siang Tiong, general manager for Southeast Asia at Internet security firm Kaspersky, said SMS remains one of the most accessible ways for organisations to reach a wider group of customers.
“You must understand that not all customers like to install apps or be savvy enough to install one. If you want to reach that wide group of audiences, you must find all possibilities,” he said.
That said, the use of SMS must be complemented with either physical or digital tokens that provide customers with one-time passwords. Banks can also explore other forms of authentication software.
While it is essential to offer customers various authentication or protection options, Mr Yeo pointed out that this adds to business costs and may also risk spreading resources too thin especially given the current shortage of cybersecurity expertise.
“These are real questions,” he added, noting that banks can explore teaming up with cybersecurity firms to beef up their defences.
Following the OCBC incident, authorities announced on Wednesday (Jan 19) more measures to bolster the security of digital banking.
These include the removal of clickable links in emails or text messages sent to customers, setting a default threshold of S$100 or lower for funds transfer transaction notifications and having a delay of at least 12 hours before the activation of a new soft token on a mobile device.
Banks will also continue to work with the authorities on other efforts, such as coming up with more permanent solutions to combat SMS spoofing. This includes the adoption of the SMS Sender ID registry.
The Monetary Authority of Singapore (MAS) is also intensifying its scrutiny of major financial institutions’ fraud surveillance mechanisms to ensure they are adequately equipped to deal with the growing threat of online scams.
"The growing threat of online phishing scams calls for immediate steps to strengthen controls, while longer-term preventive measures are being evaluated for implementation in the coming months," MAS and the Association of Banks in Singapore said.
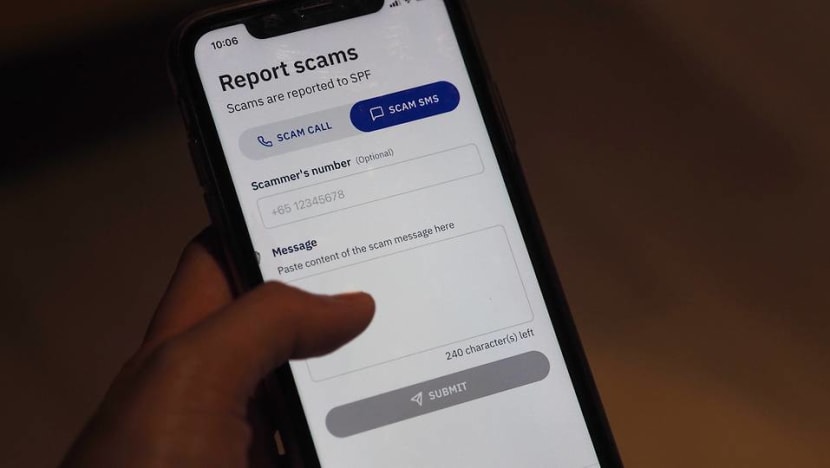
CONSUMERS NEED TO BE VIGILANT
More importantly, consumers will have to do their part and be on guard.
And with people unlikely to forsake the convenience of online banking and other digital tools, it is necessary for everyone to be aware of how to build up their own cyber defences, said Mr Yeo.
For one, never click on links provided in suspicious e-mails and text messages.
If you receive an SMS saying that there are issues with your bank account, always “go through the proper channel to check”, Mr Yeo said. This can include using the bank’s official mobile app, typing the bank's URL directly into the address bar of a web browser, or calling the bank directly for verification.
In the case of OCBC, the bank has said that it would never send messages to inform customers about account closures or that they have been locked out of their accounts. These are always communicated via physical letters.
OCBC also said it will never send SMSes with links to reactivate customers’ accounts. Such reactivation must be done in person at bank branches or via Internet banking.
People can also download security software onto their phones as additional protection, Mr Yeo said.
A study done by Kaspersky found that while most people have installed some form of protection software on their personal computers or laptops, they did not do the same for their mobile phones.
“But most of the people will do their Internet banking on mobile phones … and in the event when you click on a suspicious link, the software can catch it,” said Mr Yeo.
Another option is ScamShield, the mobile app developed by the National Crime Prevention Council and the Government Technology Agency.
The app identifies and filters out scam messages using AI, sending them to the phone’s junk folder. It also blocks scam calls from phone numbers used in other scam cases or reported by ScamShield users.
Since its launch six months ago, a total of 722,865 messages have been reported and more than 5,537 phone numbers believed to be used in scams have been blocked on the ScamShield app.